Windows Azure AD: 7 Powerful Features You Must Know in 2024
Windows Azure AD isn’t just another cloud tool—it’s the backbone of modern identity management. Whether you’re securing remote teams or streamlining access across apps, this platform delivers unmatched control and scalability. Let’s dive into what makes it a game-changer.
What Is Windows Azure AD and Why It Matters

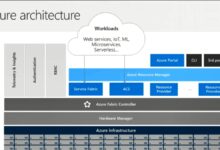
Windows Azure AD, officially known as Microsoft Entra ID (formerly Azure Active Directory), is Microsoft’s cloud-based identity and access management service. It enables organizations to securely manage user identities, control access to applications, and enforce conditional access policies across hybrid and cloud environments.
Evolution from On-Premises AD to Cloud Identity
Traditional Windows Server Active Directory was designed for on-premises networks, where users, devices, and resources were within a physical perimeter. However, with the rise of remote work, cloud applications, and mobile devices, that model became outdated.
Windows Azure AD emerged as the modern solution—built for the cloud-first world. It doesn’t replace on-prem AD entirely but extends it, offering seamless integration through services like Azure AD Connect. This hybrid approach allows businesses to maintain legacy systems while embracing cloud agility.
- On-prem AD uses NTLM/Kerberos for authentication within a local network.
- Windows Azure AD uses OAuth 2.0, OpenID Connect, and SAML for secure web-based authentication.
- It supports multi-factor authentication (MFA) by default, enhancing security beyond passwords.
“Azure AD is not just Active Directory in the cloud—it’s a completely different identity platform designed for modern application access.” — Microsoft Documentation
Core Components of Windows Azure AD
To understand how Windows Azure AD works, it’s essential to break down its key components:
- Users and Groups: Centralized identity management where users can be assigned roles and grouped for access control.
- Applications: Enterprise apps (like Salesforce, Office 365) and custom apps can be integrated for single sign-on (SSO).
- Devices: Register and manage devices (Windows, macOS, iOS, Android) for conditional access policies.
- Conditional Access: Enforce rules like requiring MFA when accessing sensitive data from untrusted locations.
- Identity Protection: Uses AI to detect risky sign-ins and automate threat responses.
These components work together to create a zero-trust security model, ensuring that every access request is verified regardless of origin.
Key Benefits of Using Windows Azure AD
Organizations worldwide are migrating to Windows Azure AD because it solves real-world challenges in identity and access management. From improved security to simplified user experiences, the benefits are substantial.
Enhanced Security with Identity Protection
One of the most powerful aspects of Windows Azure AD is its built-in security intelligence. The Identity Protection feature continuously monitors user sign-in behavior and detects anomalies such as:
- Sign-ins from unfamiliar locations or IP addresses
- Multiple failed login attempts
- Leaked credentials found in dark web scans
When risks are detected, Windows Azure AD can automatically trigger actions like blocking access, requiring password resets, or enforcing MFA. This proactive approach reduces the window of exposure during potential breaches.
Seamless Single Sign-On (SSO) Experience
With Windows Azure AD, users can access hundreds of cloud apps—like Microsoft 365, Salesforce, Dropbox, and Zoom—with just one set of credentials. This is made possible through SSO protocols such as SAML and OpenID Connect.
Administrators can configure app access directly in the Azure portal, assign users or groups, and enable self-service application access. This reduces password fatigue and helpdesk tickets related to forgotten passwords.
- Supports both cloud-native and legacy apps via Azure AD Application Proxy
- Enables passwordless sign-in using Windows Hello, FIDO2 keys, or Microsoft Authenticator
- Integrates with third-party identity providers (IdPs) if needed
Scalability and Global Reach
As a cloud-native service, Windows Azure AD automatically scales to support organizations of any size—from startups with 10 employees to global enterprises with over a million users.
It operates across Microsoft’s global network of data centers, ensuring low-latency authentication and high availability. This is crucial for multinational companies that need consistent performance across regions.
Additionally, Azure AD offers tiered licensing (Free, Office 365 apps, Premium P1, Premium P2), allowing businesses to scale features based on need.
How Windows Azure AD Integrates with Microsoft 365
One of the strongest use cases for Windows Azure AD is its deep integration with Microsoft 365 (formerly Office 365). Every Microsoft 365 subscription includes Azure AD capabilities, making identity management seamless for admins and users alike.
User Provisioning and Lifecycle Management
When a new employee joins an organization, their account is typically created in Windows Azure AD. From there, they can be automatically provisioned across Microsoft 365 services like Exchange Online, SharePoint, Teams, and OneDrive.
This automation is achieved through:
- Azure AD Connect: Syncs on-premises AD users to the cloud
- Automated User Provisioning: SCIM-based provisioning for SaaS apps
- Dynamic Groups: Users are added or removed based on attributes (e.g., department, location)
This reduces manual work and ensures consistent access policies across the digital workspace.
Conditional Access for Microsoft 365 Apps
Conditional Access policies in Windows Azure AD allow administrators to define rules that control how users access Microsoft 365 resources. For example:
- Require MFA when accessing Outlook on the web from outside the corporate network
- Block access from unmanaged devices
- Allow access only from compliant devices enrolled in Intune
These policies are enforced in real-time and can be tested using the What-If Tool, which simulates policy impact before deployment.
Passwordless Authentication in Microsoft 365
Windows Azure AD supports passwordless authentication for Microsoft 365, reducing reliance on vulnerable passwords. Users can sign in using:
- Microsoft Authenticator app (push notification or biometrics)
- Windows Hello for Business (PIN + biometric on Windows devices)
- FIDO2 security keys (e.g., YubiKey)
This not only improves security but also enhances user experience by eliminating password resets and complex password rules.
Windows Azure AD vs Traditional Active Directory: Key Differences
While both systems manage identities, Windows Azure AD and on-premises Active Directory serve different purposes and architectures. Understanding these differences is critical for planning hybrid or cloud-only strategies.
Authentication Protocols and Standards
Traditional AD relies on older protocols like Kerberos, NTLM, and LDAP—designed for internal networks. In contrast, Windows Azure AD uses modern, standards-based protocols:
- OAuth 2.0: For delegated access to web APIs
- OpenID Connect: For user authentication in web and mobile apps
- SAML 2.0: For enterprise SSO to cloud applications
These protocols are web-friendly, REST-based, and ideal for cloud and mobile scenarios.
Directory Structure and Object Model
On-prem AD uses a hierarchical structure with domains, organizational units (OUs), and group policy objects (GPOs). Windows Azure AD, however, uses a flat structure based on resources and relationships.
- No concept of domains or OUs—instead, it uses groups and roles
- Supports dynamic groups based on user attributes
- Role-Based Access Control (RBAC) replaces traditional GPOs for cloud resources
This makes Azure AD more agile for cloud environments but requires a shift in administrative mindset.
Management Tools and Interfaces
Traditional AD is managed using tools like Active Directory Users and Computers (ADUC), Group Policy Management Console (GPMC), and PowerShell.
Windows Azure AD, on the other hand, is primarily managed through:
- Azure Portal (web-based UI)
- Azure AD PowerShell (now part of Microsoft Graph PowerShell)
- Microsoft Graph API for automation and integration
- Microsoft Endpoint Manager (Intune) for device management
The shift to API-driven management enables better automation, DevOps integration, and scalability.
Security Best Practices for Windows Azure AD
While Windows Azure AD offers robust security features, misconfigurations can leave organizations vulnerable. Implementing best practices is essential to maximize protection.
Enable Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to prevent unauthorized access. According to Microsoft, MFA can block over 99.9% of account compromise attacks.
Organizations should:
- Enforce MFA for all users, especially admins
- Use Conditional Access policies instead of legacy per-user MFA
- Consider using passwordless methods like FIDO2 or Microsoft Authenticator
The Azure AD MFA documentation provides detailed guidance on deployment strategies.
Implement Role-Based Access Control (RBAC)
RBAC ensures users have only the permissions they need. Overprivileged accounts are a major security risk.
Best practices include:
- Use built-in roles (e.g., Global Administrator, Helpdesk Administrator) instead of custom roles unless necessary
- Apply the principle of least privilege
- Regularly review role assignments using Access Reviews
- Enable Privileged Identity Management (PIM) for just-in-time (JIT) access
Monitor and Audit with Azure AD Logs
Visibility into user activity is crucial for detecting threats and ensuring compliance.
Windows Azure AD provides several logging and monitoring tools:
- Sign-in Logs: Track successful and failed logins, including IP addresses and devices
- Audit Logs: Record administrative changes (e.g., user creation, role assignment)
- Unified Audit Log: Available in Microsoft 365 for cross-service tracking
- Azure Monitor: For advanced analytics and alerting
Set up alerts for suspicious activities, such as multiple failed sign-ins or admin role changes.
Hybrid Identity: Bridging On-Prem AD and Windows Azure AD
Most enterprises operate in a hybrid environment—maintaining on-premises infrastructure while adopting cloud services. Windows Azure AD supports this model through seamless integration tools.
Azure AD Connect: The Bridge to the Cloud
Azure AD Connect is the primary tool for synchronizing user identities from on-premises Active Directory to Windows Azure AD.
It supports:
- Password hash synchronization (PHS)
- Pass-through authentication (PTA)
- Federation with AD FS (for legacy SSO needs)
- Group and device synchronization
PTA is often preferred over AD FS because it reduces infrastructure complexity and improves reliability.
Password Hash Synchronization vs Pass-Through Authentication
Both methods allow users to sign in to cloud apps using their on-prem AD passwords, but they work differently:
- Password Hash Sync (PHS): Hashes of user passwords are synced to Azure AD. Users authenticate directly against Azure AD.
- Pass-Through Authentication (PTA): Authentication requests are forwarded to on-prem AD agents for validation. No password hashes are stored in the cloud.
PTA offers better security and faster sign-in times, while PHS provides resilience during on-prem outages.
Hybrid Join and Device Management
Windows Azure AD supports hybrid join, allowing domain-joined devices to also register in Azure AD. This enables:
- Single sign-on to cloud apps from corporate devices
- Conditional access based on device compliance
- Co-management with Configuration Manager and Intune
This is ideal for organizations transitioning to modern management while retaining legacy systems.
Advanced Features of Windows Azure AD Premium
While the free and Office 365 editions of Windows Azure AD offer solid functionality, the Premium tiers (P1 and P2) unlock advanced capabilities for enterprise-grade security and governance.
Identity Protection and Risk-Based Policies
Azure AD Identity Protection (available in P2) uses machine learning to detect risky sign-ins and compromised users. It provides:
- Risk detection types (e.g., anonymous IP, unfamiliar sign-in properties)
- Automated remediation workflows
- Customizable risk policies (e.g., require MFA for medium or high-risk sign-ins)
This enables proactive threat hunting and reduces response time to potential breaches.
Privileged Identity Management (PIM)
PIM (available in P2) allows organizations to implement just-in-time (JIT) and just-enough-access (JEA) principles for privileged roles.
- Admins request elevated access only when needed
- Access is time-limited and audited
- Approval workflows can be enforced
This minimizes the attack surface and ensures accountability for privileged actions.
Access Reviews and Governance
Azure AD Access Reviews help organizations maintain least-privilege access by periodically reviewing user assignments to apps, groups, and roles.
- Automate reviews for guest users, application access, or role memberships
- Integrate with Microsoft Identity Governance for end-to-end lifecycle management
- Generate compliance reports for audits
This is essential for meeting regulatory requirements like GDPR, HIPAA, and SOX.
Common Challenges and How to Overcome Them
Despite its advantages, deploying Windows Azure AD can present challenges, especially in complex environments.
Legacy Application Compatibility
Some older applications rely on NTLM, Kerberos, or LDAP—protocols not natively supported by Windows Azure AD. To address this:
- Use Azure AD Application Proxy to publish on-prem apps securely
- Implement modern authentication (OAuth) where possible
- Consider app refactoring or replacement for long-term sustainability
User Resistance to MFA and Passwordless
Users may resist new authentication methods due to unfamiliarity. To ease adoption:
- Provide clear communication and training
- Start with pilot groups before organization-wide rollout
- Offer multiple MFA options (e.g., phone call, SMS, authenticator app)
Complex Conditional Access Policies
Overly complex policies can lead to access issues. Best practices include:
- Start with simple policies and gradually add conditions
- Use the What-If Tool to test policy impact
- Document all policies and maintain a rollback plan
What is Windows Azure AD used for?
Windows Azure AD is used for managing user identities, enabling single sign-on to cloud and on-premises applications, enforcing security policies like MFA, and protecting against identity-based threats in hybrid and cloud environments.
Is Windows Azure AD the same as Active Directory?
No, Windows Azure AD is not the same as traditional Active Directory. While both manage identities, Azure AD is cloud-native, uses modern authentication protocols, and is designed for web and mobile apps, whereas on-prem AD is designed for internal network resources.
How do I enable MFA in Windows Azure AD?
MFA can be enabled through the Azure portal under “Users > Multi-Factor Authentication.” However, Microsoft recommends using Conditional Access policies for better control and scalability.
Can I use Windows Azure AD without Microsoft 365?
Yes, Windows Azure AD can be used independently of Microsoft 365. It supports standalone subscriptions and can manage access to third-party SaaS applications, custom apps, and on-premises resources via Application Proxy.
What is the difference between Azure AD Free and Premium?
Azure AD Free includes basic identity and SSO features. Premium P1 adds conditional access, access reviews, and hybrid identity. Premium P2 includes advanced security features like Identity Protection and Privileged Identity Management.
Windows Azure AD has evolved into the cornerstone of modern identity management. From securing remote access to enabling passwordless authentication and advanced threat protection, it empowers organizations to embrace digital transformation without compromising security. By understanding its architecture, integrating it effectively with existing systems, and leveraging premium features, businesses can build a resilient, scalable, and secure identity foundation for the future.
Recommended for you 👇
Further Reading: